Compliance is a rite of passage for startups growing and going upmarket to meet their customers' expectations. However, as an engineer, I always felt the word had a negative connotation.
Last year, I drove Apify’s SOC 2 initiative, which shifted my perspective. This article includes the info I wish I had when starting this journey.
What is SOC 2?
Let’s step back. What do we want to achieve with the security framework?
As a CTO, I want all our SaaS or PaaS vendors to deliver their services securely—at least as secure or more secure than we do, as otherwise, they lower our derived security standards. Therefore, any SOC 2-compliant company wants all its critical vendors to be SOC 2-compliant.
But what does the actual vendor pipeline delivering service to customers look like?
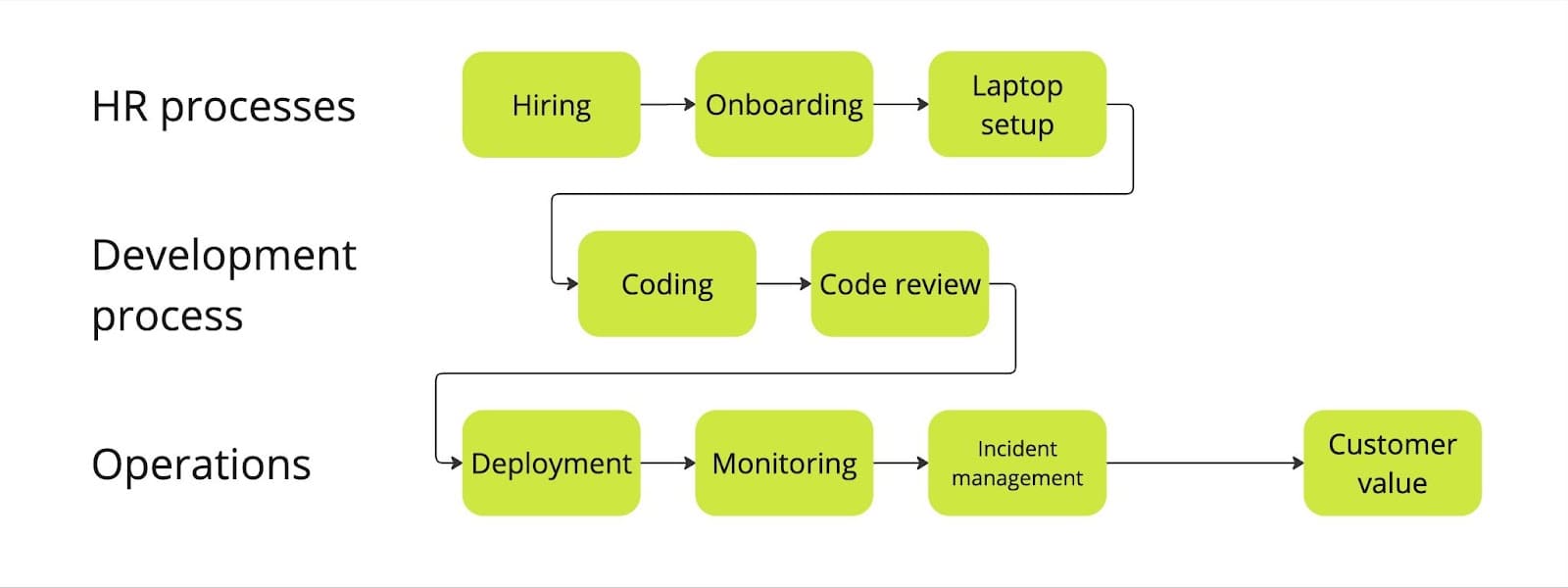
An important revelation is that security does not start with development but already with how we hire and onboard people, with risk management, and then goes all the way through coding, reviewing, and deploying to the customer.
This is what SOC 2 is about - describing how the company works across roles and departments and aligning it with best practices captured by the framework. It touches all three layers: company (people and processes), code, and underlying infrastructure.
There are two types of SOC 2 audits. Type I evaluates whether controls are designed properly at a point in time, whereas Type II evaluates whether controls are designed and functioning as intended over a specified period of time.
For obvious reasons, your customer's security information officer only cares about Type II.
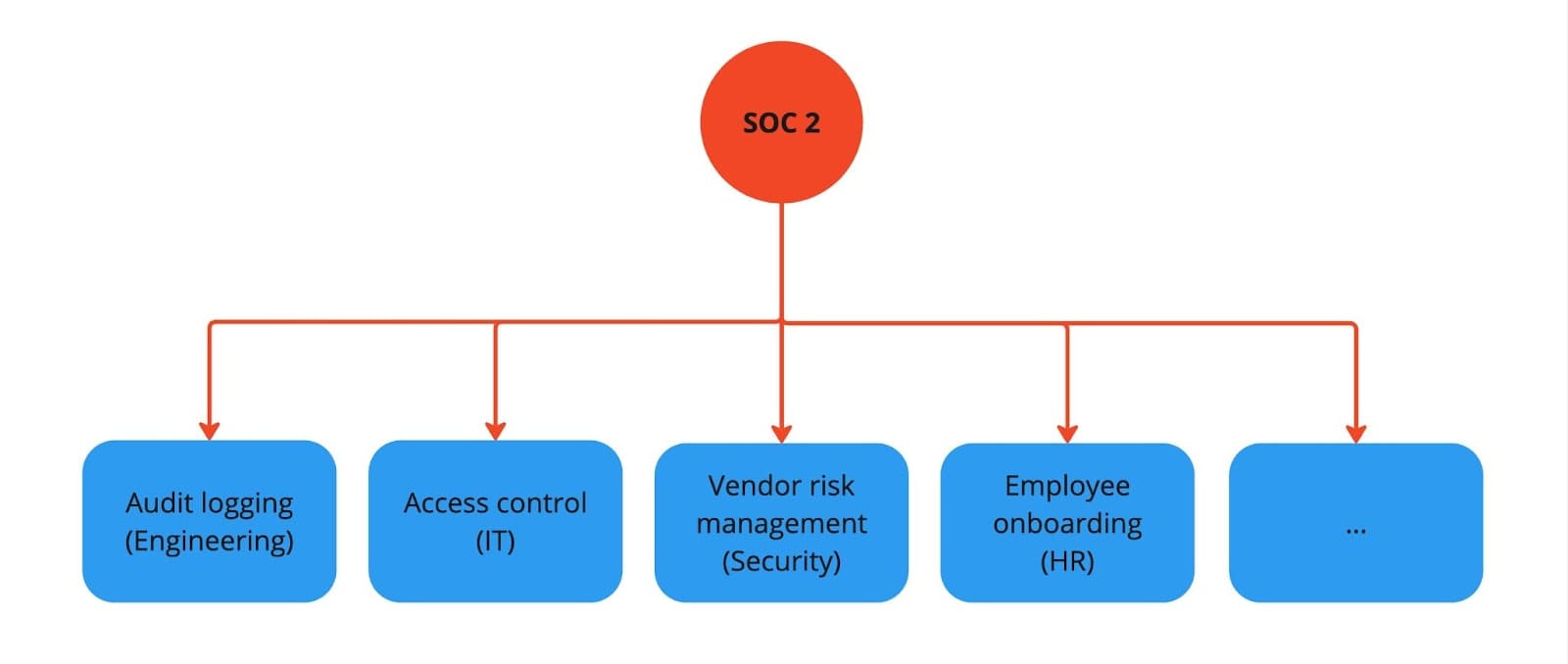
The SOC 2 framework is composed of over 80 controls that are relevant to various departments (HR, engineering, IT, operations). Example controls are:
- Confidentiality Agreement acknowledged by employees
- Infrastructure performance monitored
- Vulnerability and system monitoring procedures established
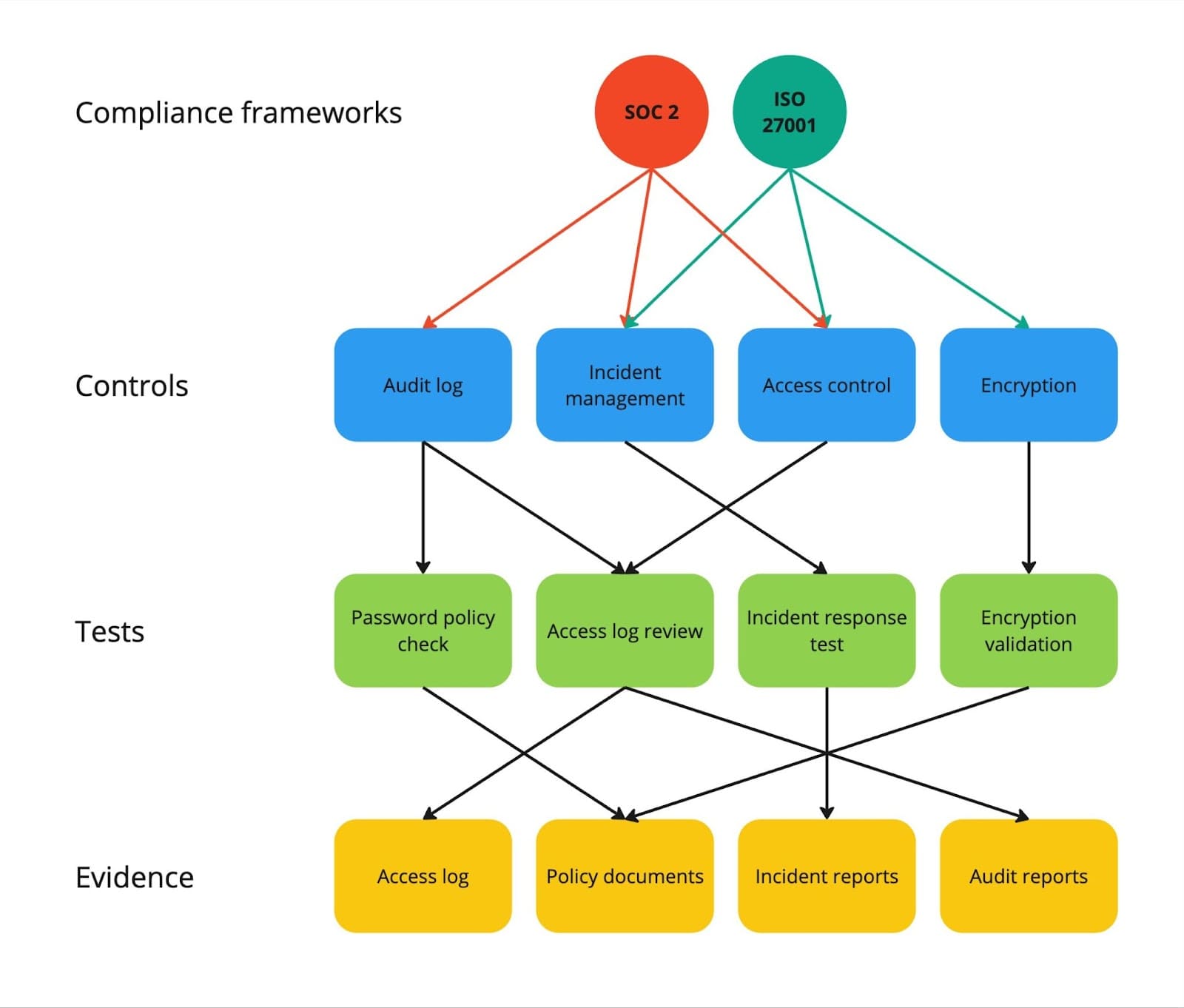
The ultimate goal of compliance is to describe how the company works with policies implementing these controls and then prove that the policies are followed, repeating the proof every year from now on.
That sounds like a vast and time-consuming effort, right? Not necessarily.
Compliance automation
Today, compliance automation platforms can help you achieve a lot. Many are on the market, and Vanta, Drata, and SecureFrame are leading. We chose Vanta as #1.
The compliance platform will do 3 things for you to speed up the whole process from months to weeks of preparation:
1. Breaking down controls into simple tests
As I mentioned, the frameworks are composed of controls that are not straightforward to comply with or document. Vanta breaks these controls into simple tests, each clearly describing one requirement. This has 2 positive outcomes:
- Compared to full controls, these simple tests are much easier to document with evidence or even automate evidence collection. Also, they break a single control into tests relevant to different departments (IT vs. HR).
- If you aim to comply with multiple frameworks, let’s say SOC 2, ISO 27001, and GDPR, the tests are largely shared despite the fact that these frameworks are composed of different controls. So, by being done with SOC 2, you are 50% done with ISO 27001.
2. Creation and adoption of policies
Once you have the controls, describe how the company works with policies. Vanta has a good policy template set aligned with how every modern tech startup works. This is where you need to sit with HR and legal to adjust the template policies to your company processes. Having good start material saves a lot of time than starting from scratch. In the end, you end up with a similar set:
| Human resource security policy |
| Code of conduct |
| Third-party management policy |
| Risk management policy |
| Asset management policy |
| Data management policy |
| Cryptography policy |
| Secure development policy |
| Access control policy |
| Business continuity and disaster recovery plan |
| Operations security policy |
| Physical security policy |
| Information security roles and responsibilities |
| Information security policy (AUP) |
| Incident response plan |
3. Evidence automation
Now, you have policies and must prepare evidence for auditors proving that you follow them. If you use mainstream tooling (Google Workspace, AWS, BambooHR …), then Vanta integrates into your ecosystem to collect the evidence. Here are some examples of what we automated with Vanta:
- HR system (BambooHR)
- Offboarding of people is completed within the SLA
- Background checks are done on new hires within the SLA
- Identity provider (Google Workspace)
- MFA on the identity provider is enabled
- An identity provider is used
- Cloud provider (AWS)
- Public SSH is denied
- Unwanted traffic is filtered
- User data is encrypted at rest
- Data store (MongoDB)
- MongoDB clusters are backed up
- MongoDB clusters are encrypted
- Version control (GitHub)
- P3 security issues are resolved within the SLA
- Application changes are reviewed
- Code is scanned for vulnerabilities
- Medium vulnerabilities identified in packages are addressed
You should be able to automate ¾ of the documentation this way if your tooling is compatible with a compliance automation platform and you need to provide evidence manually for the remaining items
Besides this, Vanta provides a risk register within their platform, people onboarding (everybody must accept relevant policies, watch a security training video, …), and basic mobile device management client that makes sure every employee has:
- Encrypted laptop
- Password manager and antivirus installed
- Screenlock on
This is the security bare minimum everybody should follow anyway.
Have a battle plan
To prepare for this challenge, have a small tiger team with people from engineering, HR, and legal. Start with policies, adapt them to your work style, and then jump on their adoption and evidence collection. The preparation took about two months, proving we were already well set up.
Reach out to auditors roughly about a month before the planned audit. You may do this via your customer success contact in the compliance platform. We chose Prescient Security based on recommendation.
An external penetration test is an important part of any security compliance. Most auditors also provide penetration testing. We found an independent one, as good practice is to utilize different companies for penetration testing every year to increase coverage.
Finally, once done, you can publish your Trust Center to inform customers and collect potential enterprise leads.
SOC 2 tips: What we’ve learned
Here are some more tips from our journey:
- You can skip the SOC 2 Type I audit and go directly for Type II, saving on audit costs and time. There is no advantage in getting both, and nobody cares about Type I.
- You must establish some new processes if you don’t have them yet. In most cases, you don’t need specialized tools and platforms for vendor management, access management, access requests evidence, … . You can utilize Slack, spreadsheets, and other existing tools, at least for a start.
- On the other hand, you don’t want to be doing background checks on your own. Find a good vendor instead.
- Start soon. It’s so much easier to pass an audit as a company of 40 people rather than a mature company of 120.
With the right automation, the whole process is smooth and helps to find gaps in the organization. We didn’t have to change how we work, yet we gained a lot of value and made the company more resilient.