Apify is introducing a new account-level setting called general resource access. This setting lets you choose whether your storages, runs, and builds can be accessed through their unique ID or require authentication to provide an additional layer of security. If you’re a public Actor developer, read below to make sure your Actors will keep working well.
How general resource access works
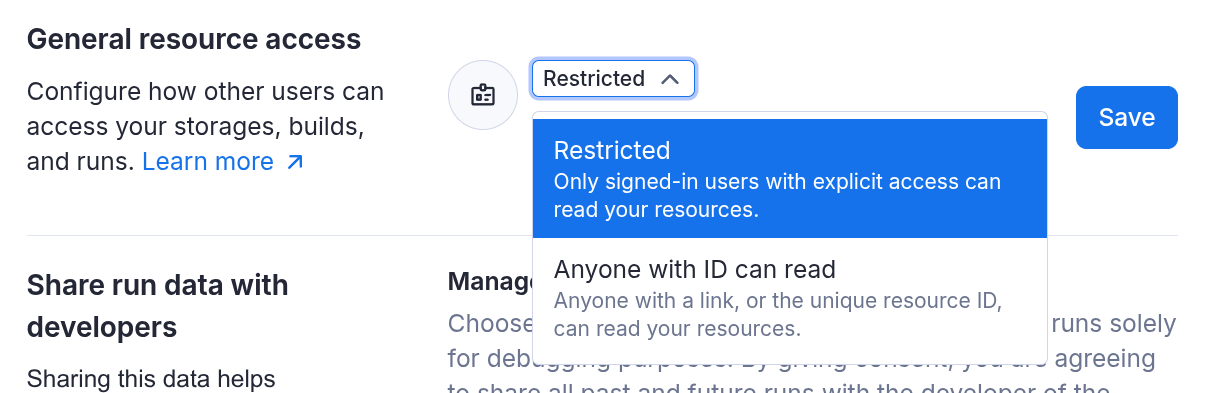
You can find general resource access in Apify Console under Settings → Security & Privacy. The setting has two options:
- Anyone with ID can read: The existing, default behavior. Anyone with the unique resource ID can read the resource. This allows sharing by link.
- Restricted: The new option. Only signed-in users whom you have given access to can read your resources.
To understand the practical effect, consider the following Apify API call to download dataset items:
https://api.apify.com/v2/datasets/><UNIQUE_DATASET_ID>/items?clean=true&format=json
If your general resource access is set to anyone with ID can read, you can just send this link to anybody, and they will be able to download the data even if they don’t have an Apify account. However, once you change the setting to restricted, this API call will require a valid token with access in order to work. In other words, you’ll have to share the dataset explicitly, and you can only do that with people who have an Apify account.
Note that only storages, runs, and builds are affected by this setting. Other resources – like Actors, tasks, or schedules – always need to be shared by their owner, either via access rights (the share dialog) or an organization account.
Why we’re introducing general resource access
Sharing by link is a fast and convenient way to collaborate with other people. Thanks to the hard-to-guess, unique IDs, it’s also secure enough for most use cases.
However, it doesn't offer features like access revocation or a formal audit trail. Users who need these capabilities can use general resource access, as it gives them more direct control over who can access their data.
What is the best setting for me?
The existing, default behavior is still a good choice for most users, as it balances security with convenience.
The restricted access is useful for users with higher security and access control needs, in particular if they are heavily integrated with third-party services and rely on scoped API tokens (read more below).
You can try enabling the restricted access to get the new features, but if it impacts your workflows, you can always go back. Note that while we’re introducing the setting, some existing public Actors and integrations might not support it yet. Their authors need to update them to provide a valid token on all API calls.
How to collaborate with restricted resource access
Enforcing restricted access doesn’t mean you can’t collaborate efficiently. Sharing via access rights (the share dialog) or an organization account still works. On top of that, we have introduced a few features for your convenience.
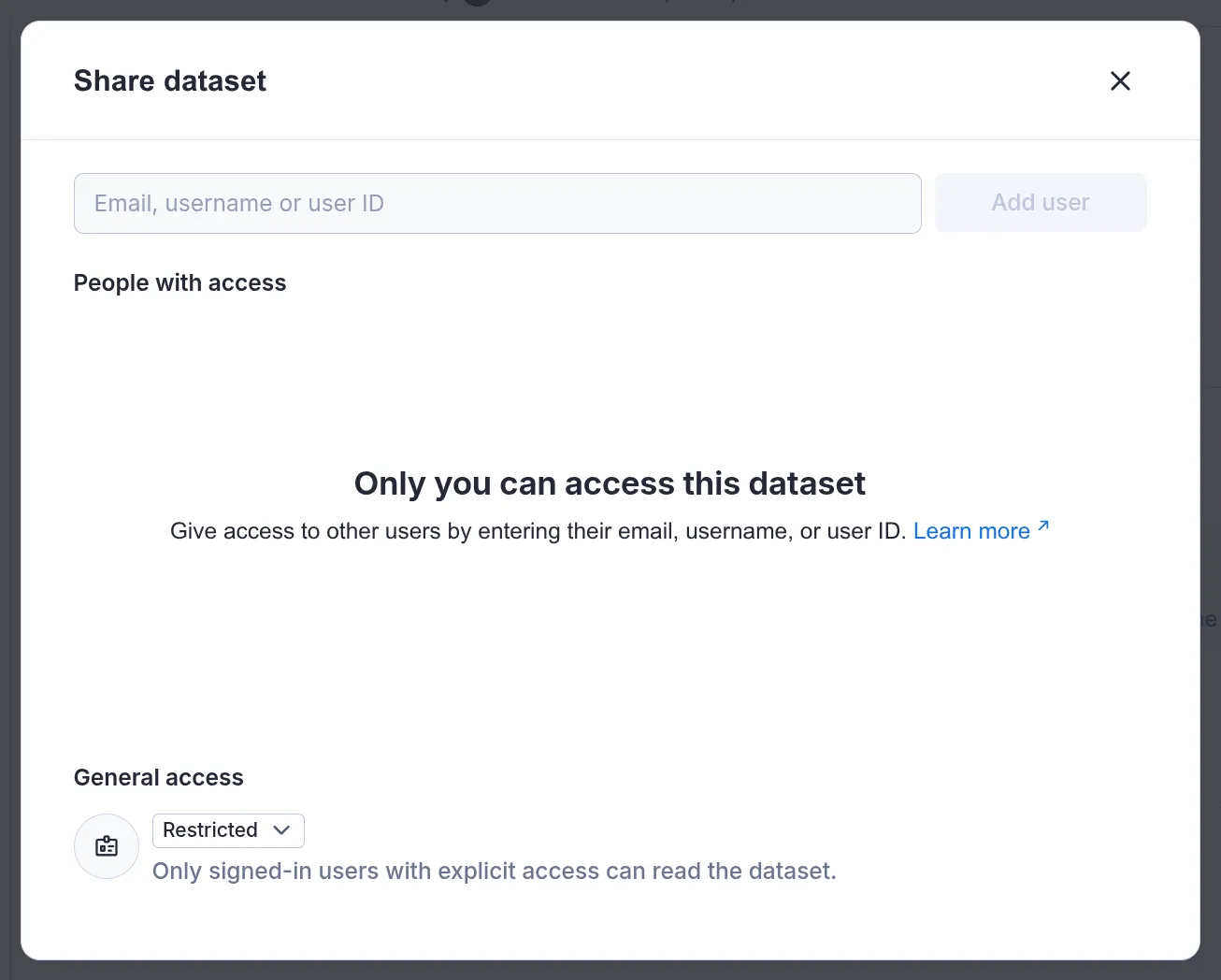
For one, the share dialog has been updated, and it now allows you to override the general resource access on individual resources. For example, you can set Anyone with ID can read just on a single dataset that you want to share quickly by its link. That way, everything else on your account stays protected.
Refer to the documentation for more quick-sharing tips, such as Console storage deeplinks and signed key-value store record URLs.
Implications for public Actor developers
If you own a public Actor on Apify Store, you should double-check that your Actor will work even for users who have restricted access to their resources (note that the setting on your developer account has no impact here).
In practice, this means that all API calls originating from the Actor need to have a valid API token. If you are using Apify SDK, this is the default behavior. Check out the documentation for a more detailed guide on how to make sure your Actor supports users with restricted access.
Update on scoped API tokens
Some time ago, we introduced scoped API tokens, which can limit the access of integrated third-party services when interacting with your Apify account.
If you use scoped API tokens, you can greatly benefit from the restricted resource access, as it allows scoped tokens to provide stronger security guarantees. It also simplifies scoped token configuration, as it makes it easier to reason about what the token can and cannot access.
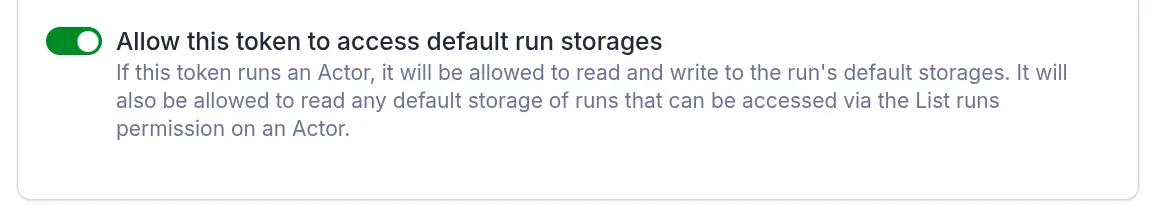
As part of the work on general resource access, we added a new toggle that controls the token’s access to default Actor run storages:
- If it’s on, the token can implicitly access the default storage of the Actor runs it triggers, or in general, of any Actor run in your account that falls within its scope. This is useful if you want to allow a third-party service to run an Actor and then read the Actor’s output (think AI agents).
- If it’s off, it can only access the Actor run, but not its default storages. This is great for fire-and-forget integrations.
Get started today
General resource access is now available to all users. To configure it, head over to your security and privacy settings. For a complete guide on how this feature works, see the documentation.