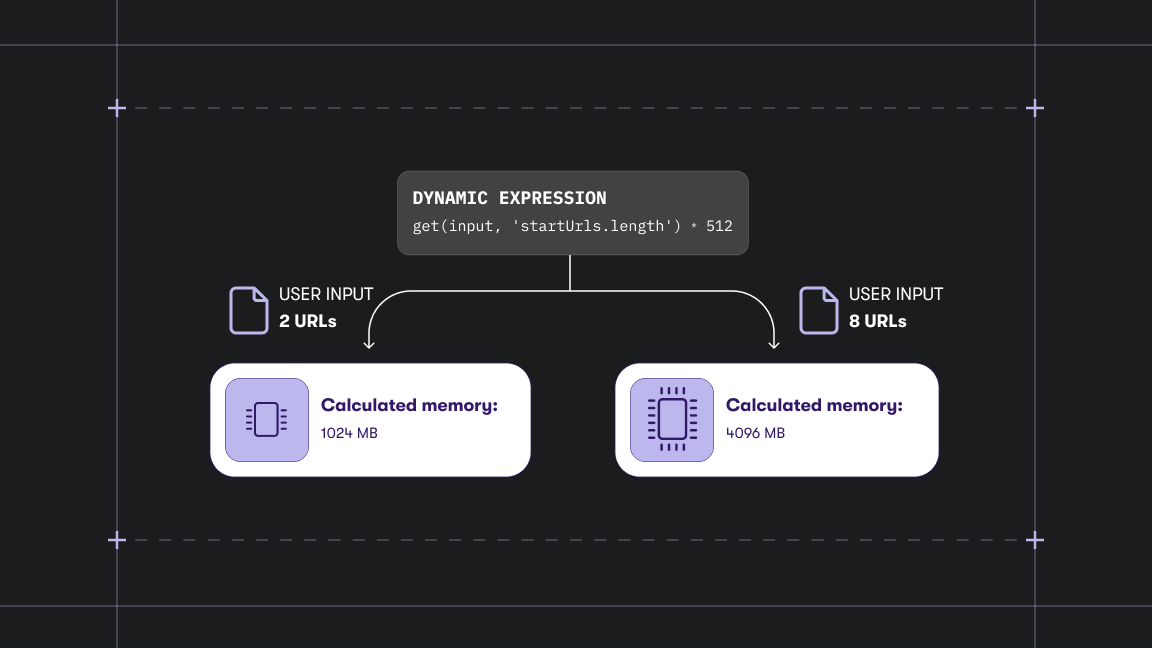
As the leading platform and marketplace for web scraping and web automation tools, with thousands of developers and companies building their products with Apify, we are committed to providing a secure and compliant environment.
This year, we made significant investments in our security program to ensure that our platform, security controls, and processes meet the highest standards of security and compliance.
SOC 2 compliance
We proudly announce that Apify has completed the SOC 2 Type II audit. As a mature company with a large and complex system, this process required significant effort from every department.
Apify was independently audited by a third-party auditor, Prescient Security, for three trust service criteria (TSCs): Security, Availability, and Confidentiality. Part of the audit was third-party penetration testing of our platform.
We use the leading compliance automation tool, Vanta, to ensure that our processes across departments - ranging from HR to engineering - and our infrastructure comply with the SOC 2 framework every day.
What does this mean for you?
- Enhanced data protection: SOC 2 compliance ensures that our systems and processes are designed to safeguard your data against unauthorized access and data breaches, providing you with enhanced security measures.
- Reliability and availability: Our SOC 2 compliance demonstrates our commitment to maintaining a highly reliable and available service, ensuring your operations run smoothly without disruptions.
- Privacy assurance: Adherence to privacy principles under SOC 2 means that your sensitive information is handled with the highest level of confidentiality and integrity.
- Trust in compliance: By meeting these rigorous standards, we affirm our dedication to compliance and operational excellence, allowing you to trust in our ability to meet your needs and regulatory requirements.
- Risk mitigation: Our SOC 2 compliance helps mitigate risks associated with outsourcing services, giving you peace of mind that we are continuously monitoring and improving our security practices.

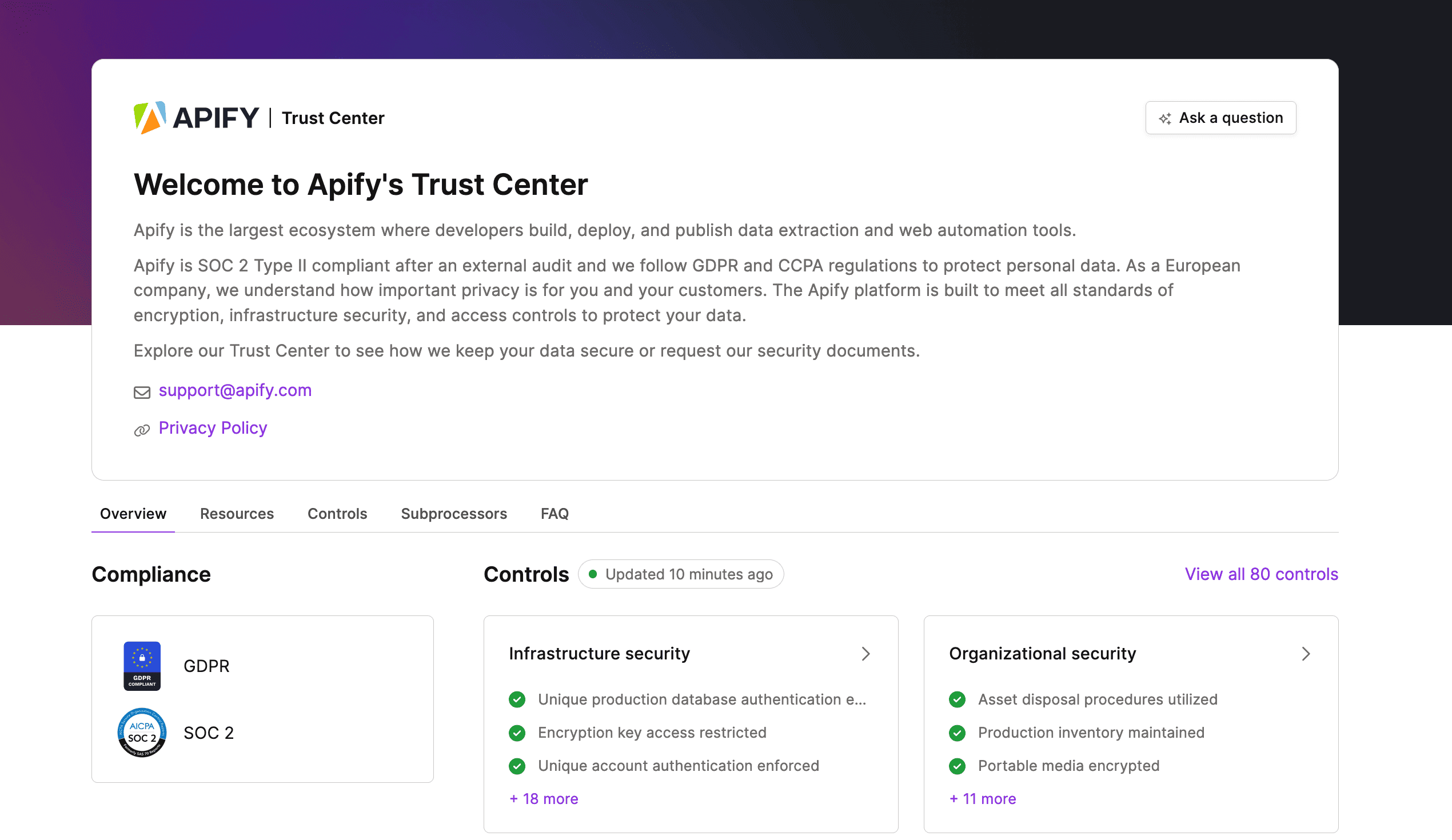
Trust Center
We have also launched a new Trust Center where you can find information about our security and compliance programs, including our SOC 2 Type II report. You can access the Trust Center at trust.apify.com.
The Trust Center is updated in real-time whenever we obtain a new certification, audit report, or change to our security and compliance programs.
Take better control of your organization's security
In addition to compliance efforts, we have also implemented new security features for organizations. We know that security is a team effort. That’s why we’re introducing tools to help you ensure security best practices among all members of your organization:
- Mandatory two-factor authentication: To reduce the risk of unauthorized access, ensure that all members of your organization have 2FA enabled.
- Session length limits: Set maximum session durations for all members, providing added protection by requiring periodic re-authentication.
Head over to the organization settings to set and enforce your preferred security standards.
What's ahead of us?
This is an ongoing commitment for us. We have established security as a strong competence in our organization. In 2025, we plan to introduce a new permission system to strengthen control over your data and usage, elevate our bug bounty program, and more.
Thank you for your continued trust in Apify!